What happens during a spoofing attack?
Ramya Sriram
6 min read
1st Jul, 2024
GPS spoofing
Imagine the scenario:
You’re due to meet someone after work. It’s peak traffic and your satellite navigation system is already indicating your arrival time that will make you late. With bad traffic, your GPS navigation takes you via an unfamiliar route… but a GPS spoofer is nearby who will disrupt your plans…
There have been known incidents such as this where relying on your GPS for car navigation has led to unexpected and even dangerous situations due to GPS interference. There are hundreds of potential scenarios that could play out, depending on the intent of the attacker, but here we will look at one and consider driver controlled vehicles and automated vehicles.
As the driver of a vehicle, you can always remain in control of the vehicle and at any given opportunity, you can overrule your navigation system’s instruction. However, with the increasing use of autonomous vehicles, the instincts that manual drivers rely on may not come into play, making it crucial to examine how Advanced Driver Assistance Systems (ADAS) would handle the potential threat of GPS spoofing.
In this blog, Ross van der Merwe, GNSS Engineer at FocalPoint, explains the potential impact of what could happen during a GPS spoofing attack.
What happens during a spoofing attack?
During the attack, authentic GNSS signals are transmitted from the individual satellites across the sky. The fake signals however will be broadcast from a single location close by, therefore easily overpowering the real (but relatively weak) GNSS signals.
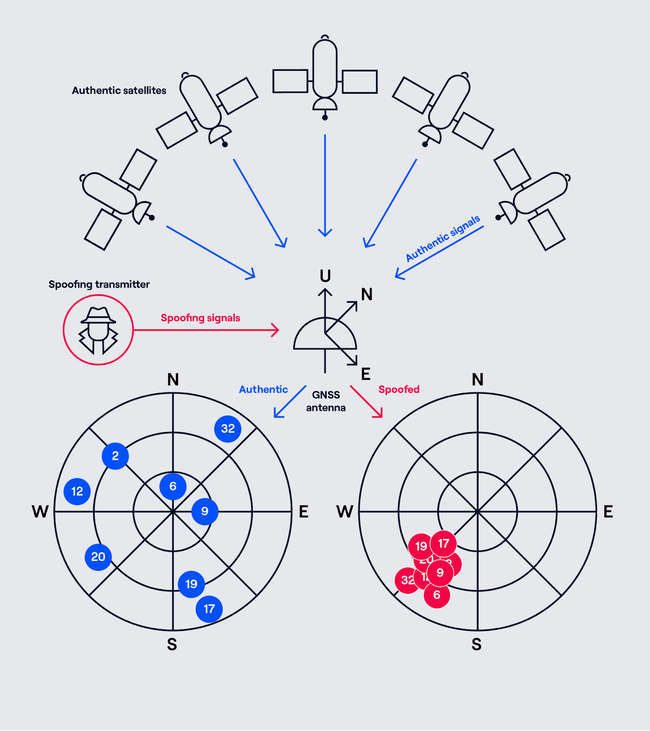
Figure 1 – Distributed authentic vs spoofed GPS signals transmitted from a single location [1]
Back in the car again:
You reach a set of traffic lights, your GPS starts to behave strangely: it starts moving off unexpectedly even though you are at a stand still. As it ‘drives’ away the navigation software starts rerouting, now telling you to make a u-turn. As the lights turn green, you are left confused about what to do next or where to drive…
This could be a typical scenario of a GPS spoofing attack that you could face. As the driver, you were in control. Although this situation could be distressing or even dangerous (in 2022, over 12,000 accidents were attributed to driver distraction or impairment [2]), at least as the driver, you were able to recognise something was wrong and take corrective action.
The attacker’s goal could be to influence the positioning system in order to take control of the vehicle, impacting where the car is heading.
With increasing autonomy associated with Level 4 and 5 Advanced Driver-Assistance Systems (ADASs) backup systems should always kick in causing no harm to the driver. The question is, how would the system respond to a spoofed navigation and adapt its guidance?
In the worst case scenario, your system is fooled by the spoofing and is tricked to drive down a narrow dangerous ally, just like the attacker intended. Another possibility is that the vehicle stops in the middle of traffic, leading to distress and further traffic issues. A basic, but robust, system might see something is off, and ask the driver to intervene. A better system could detect spoofing and exclude GPS (losing the benefits of an independant absolute positioning) and rely on other navigation, like cameras, radar, and lidar to get you safely to your destination. An excellent system could detect and mitigate the spoofing (retaining use of trustworthy GPS positioning) and regain full control of all sensors, resulting in a smooth ride.
Improved safety & regulation
Improved regulation to address the threat and addressing system robustness is of course key to spoofing mitigation, essential for consumer acceptance around increasing levels of automation.
With the numerous reports of spoofing attacks happening near conflict zones, and the wide impact to neighboring countries, it is becoming more clear that indeed GPS spoofing is a threat that must be handled in the civilian domain. Currently the likelihood of being a victim is low, but it only takes one attack to negatively impact you.
How to protect yourself from spoofing attacks
As technology continues to advance, so do the techniques used by GPS spoofers. To stay ahead of these malicious actors, it is crucial to use the right technology to improve GPS spoofing prevention. One solution is the development of software that can better detect and reject spoofed signals. A software upgrade to existing GPS receivers, S-GNSS, provides improved accuracy, sensitivity and multipath mitigation. It also provides a completely new category of measurements for a single-antenna GPS receiver: angle of arrival (AoA). It is through the discrimination of arrival direction that S-GNSS can identify, ignore, and (if required) locate the source of spoofing.
Interested to learn more about spoofing? Download our comprehensive white paper on GPS spoofing and cyberattacks. Download now
References:
[1] Adapted from J. R. van der Merwe, A. Rügamer and M. Lipka, “Enhanced Spatial Spoofing Detection With and Without Direction of Arrival Estimation,” IEEE Transactions on Aerospace and Electronic Systems, vol. 59, no. 5, pp. 5530-5540, Oct. 2023, doi: 10.1109/TAES.2023.3262455. with permission.
[2] Reported road collisions, vehicles and casualties tables for Great Britain: https://www.gov.uk/government/…







